Reuven Aronashvili has always been obsessed with solving problems and standing out from the crowd – and to understand the man himself, helps you understand his business.
The CEO of Israeli cybersecurity firm CYE has a compelling story. He has consistently excelled throughout his life, firstly as an award-winning student and later as a co-founder of the Israeli army’s Red Team (Section 21) and Incident Response Team in Matzov (the Hebrew abbreviation for Center of Encryption and Information Security), and more recently as an entrepreneur.
Such was his academic prowess in his youth, he admits he became bored by the standard curriculum and sought diverse ways to stimulate and engage his brain.
The included watching card games where he became intrigued by the probability and risk factors and how someone playing could create a situation where they would always, or more often than not at least, win.
“You learn very quickly that being an attacker is much easier than being a defender in life,” says Aronashvili, reflecting on the formative years of his life and career.
“So, when I got to the Army and I got to, in some way, shape my own destiny, that was quite nice to achieve. I was one of the founders of the Israeli Red Team, where we got military-grade training to be able to use offence tools, offensive capabilities to demonstrate the cybersecurity maturity level of the organisation.
“I think my contribution to the Israeli nation and to the Army was significant, and that’s something that was also important to me on a personal basis as well, contributing to improving cybersecurity capabilities, the defensive capabilities of our nation.”

You learn how to develop both capability, integrity, and to know what is wrong, what is right – and that's a very important thing that still has influence on what we do today
Aronashvili, who now serves as a trusted advisor for executives in leading Fortune 500 companies, admits there were multiple occasions where he and his team were on one hand impressed by the level of offensive capabilities, from a technical standpoint – but they were also acutely aware that the impact could be counted in the millions or hundreds of millions in some cases. In other cases, there was also a potential risk to human life when critical infrastructures (such as electricity, the oil and gas environment or nuclear environment) were under attack.
“In the first 12-to-24 months of the team, we were able to get to touch the most important parts of the Israeli infrastructures and critical systems.
“With that experience, you start to understand the power of what you do, because you’re getting tools or weapons, which in the wrong usage can be harmful. You learn how to develop both capability, integrity, and to know what is wrong, what is right – and that’s a very important thing that still has influence on what we do today.”
It was a highest level national defence-critical cybersecurity remit. And when he left the army, it was very quickly clear that Aronashvili would have to go his own way to continue to operate in a way which proved stimulating to him.
Aronashvili, who is unsurprisingly certified by the U.S. Department of Homeland Security as a world-class ICS and SCADA cybersecurity expert, describes the one job interview he had after leaving military service as being rather dispiriting with the company involved operating at a “significantly lower level” than he expected. He talks about how he didn’t want to end up in a situation where he felt “like a lawyer charging billable hours”.
Instead, he founded CYE, firstly as a small shop in October 2011, before the company was incorporated at the beginning of 2012.
Just over nine years later and CYE – which stands for “cyber-eye” but is pronounced “sigh” – has over 200 customers across the globe, including the likes of UBS, Investec, the World Economic Forum and General Electric.
“It’s part of my approach and part of my character, to always be above and beyond,” he says. “The urge to excel and be really excellent at everything that you do, that’s something that is part of my culture. If you can’t do it to the best of your ability, don’t do it at all.
“And when I founded this company, this was and still is the approach. We’re not doing everything, we’re only doing the things that we can be the best at and can provide the best value-add for our customers and our partners.”
CYE employs 70 “ethical hackers”, each with at least six years of military experience, using its proprietary software, Hyver, and the company employs around 100 people overall globally.
But what makes CYE so interesting is the innovate, offensive approach the company takes to cybersecurity, breaking into clients’ systems with the same approach rogue hackers would take, in order to deliver an adaptive solution which can prevent any multitude of threats.
It does that “by utilising data, numbers and facts”, to predict risks. And then, by employing critical thinking and “producing disruptive ideas”, CYE tailors practical solutions which focus on the areas most critical to customers’ key business assets.
An interesting aspect is how Aronashvili’s military experience has translated into a commercial context.
He describes an engagement where, from beginning work with a pharmaceutical company to help improve its cyber security level of their manufacturing lines, CYE then worked with private equities and helped the same company to make a $1billion deal. There was a specific opportunity in which cybersecurity was set to scupper the deal. CYE came in and ramped up cybersecurity capabilities and six months later the deal happened.
Aronashvili cites an example where, simply by hacking into an airline client’s security ecosystem, CYE was able to identify a specific foreign government attack, where private information of citizens worldwide was breached.
“We were able to identify this specific hacker, which was in the organisation while we were doing our own security assessment,” he says. “We were attacking the organisation to identify the gaps, and then you get into a specific place and you see that someone is already there.
“We exposed a nation-level attack and we found ourselves then managing the situation and actually taking the organisation through the steps to remediation and eradication of those specific threats moving forward.”
Aronashvili though, is an advocate of prevention instead of cure, and there is a three-step methodology which comes into play when CYE engages with a client.
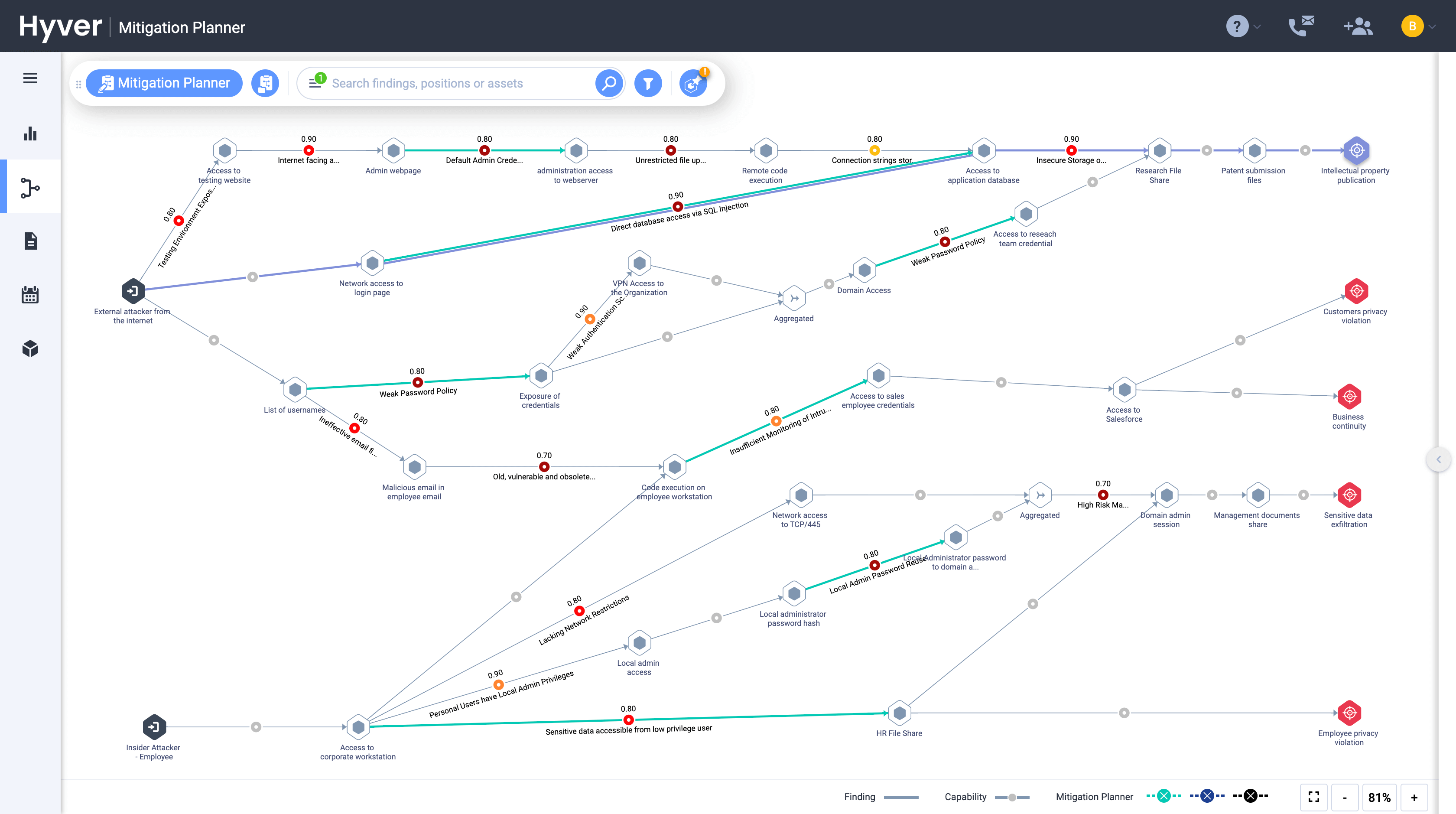
The first stage is visibility. CYE starts by evaluating the organisation, identifying the business-critical assets, then the potential threat sources that can threaten those specific assets. CYE then executes an “offensive exercise” to uncover all the relevant vulnerabilities that we are able to identify in the organisation.
The second stage is to assess the realistic threat level of each risk and how vulnerabilities and business critical assets may be exposed. CYE generates a structured and graphical demonstration of what can happen in the organisation, what would be the potential modus operandi of the attackers that will be used against the organisation. Its tool provide an accurate measurement of how likely this is to happen and what the financial impact would be of compromising each specific business asset. The organisation’s overall exposure is also assessed at this point, with real-time support and real-time risk evaluation is provided, as the situation is always fluid.
The third stage is then mitigating those risks. That involves evaluating the cost for fixing the items that were identified, what the order should be in terms of addressing those issues and how to optimise the cybersecurity investment for the client using optimisation algorithms.
It’s at this point that Aronashvili mentions the company’s proprietary platform, Hyver.
“Those three steps take the organisation through a cybersecurity improvement process which can be implemented in a way that we can measure success and demonstrate that the organisation has actually improved their cybersecurity,” he says.
“The Hyver platform works in the same order. The first part is the offensive system, the second is the risk translation part in which we are looking at the technical instabilities, and the third part is the mitigation optimisation platform, which uses predictive analytics allowing us to anticipate the next potential threats against the organisation and, based on that, we can estimate the costs and the effort needed in order to mitigate.”
Hyver certainly has some very impressive cutting-edge technologies built-in and CYE is constantly improving the platform.
“We have machine learning capabilities and AI capabilities in our system,” Aronashvili continues. “We have a lot of subsystems in which we use a lot of AI capabilities in order to evaluate social networks and Google hacking techniques in order to identify the data and to evaluate which assets belong to which organisation. That’s something which used to be manually done and required a lot of resource; today we do that in an automated way that provides very high value to what we do. What took weeks before, we now do in less than an hour.
“That’s very, very significant from our point of view. Not everything that we do is based on AI and machine learning though. There are some things that are very deterministic. For example, when we evaluate what is the priority of mitigating items, ‘what is the risk level?’. That’s something that we won’t use artificial intelligence for.”
We are looking to build a very significant capability in the market and be a significant influencer in the cyber security market.
It’s an impressive platform, a company with a very innovative way of working and CYE is also poised now for some rapid expansion following a $100 million investment in a round led by global investment firm EQT.
But Aronashvili reveals to Digital Bulletin that the total cash injection was actually around $120million, when taking into account other investors who joined under various specified parameters.
“It was really the balance between creating something that is interesting enough for our partners, and to work with them, while making sure that we are not diluted too much,” he says. “Now, instead of doing things one-by-one, we were doing things in parallel. That means expansion to different parts of the world.
“We always want to expand to new markets. Now, instead of doing that one-by-one, we are going to do that in parallel, going after different markets at the same time.
“More than that, we are going to look at new acquisitions, potential acquisitions for acceleration of the technology development or the go-to-market capabilities if we want to develop.
“We have a very strict and ambitious plan at the moment and hundreds of percentages of market cap and specifically access to different markets that we have now as target markets. So, this is a journey of forces that we are executing at the moment and it’s a very exciting one!
“We are looking to build a very significant capability in the market and be a significant influencer in the cyber security market.”